In late January, hackers stole $530 million from the Coincheck Exchange in Asia, taking money from 260,000 clients with deposits of NEM, a lesser known cryptocurrency. NEM lost 20 percent of its value, but regained it almost immediately. A few days later, Line, a popular messaging app in Japan, launched its own cryptocurrency/digital exchange for its 170 million users.
"Cryptocurrency exchanges are making fat profits right now," said Koji Higashi, a Japanese Bitcoin entrepreneur and commentator. "Mainstream companies such as Line are now trying to take advantage of this growing market."
As these two virtually simultaneous events indicate, the massive fluctuation and appreciation of cryptocurrencies value—Bitcoin was valued at $19,850 in December, but less than $8,000 in February—has generated a lot of recent hype and attention from governments, banks, consumers, and criminals.
But, much less attention has been paid to the industrial architecture that supports digital assets such as Bitcoin or Ethereum. From our perspective, before speculating about potential market value in the short and medium term, either for commercial banks or large-scale consumer adoption, it is mandatory to ask whether the cryptocurrency system, in general, is reliable and secure.
A Primer on High-Level Cryptocurrency Network Architecture
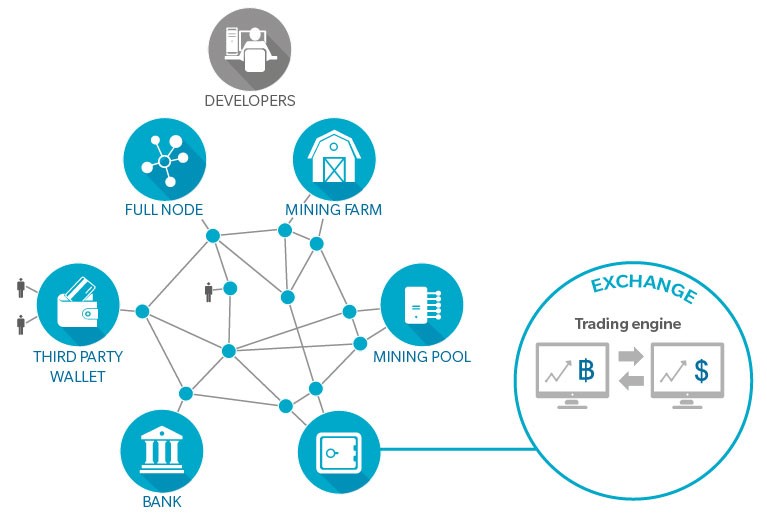
Online interactions among four categories of actors constitute what is called the Bitcoin network: Developers, Nodes, Miners, and Third-Party Service Providers.
1. Developers maintain the Bitcoin protocol and open-source software. Few people have release rights for the “Bitcoin Core”.
2. Nodes act as accountants. They store a copy of the ledger of all confirmed transactions; receive, validate, and broadcast transactions yet to be confirmed; and receive, verify, and broadcast blocks of confirmed transactions. Nodes add verified blocks to their own copy of the ledger to create a chain of blocks (hence the term “blockchain”). Anyone with a reasonably powerful computer can set up a full node.
3. Miners expend computational power to generate blocks of verified transactions and collect a reward for solving cryptographic riddles. The first miner to solve the cryptographic riddle associated with the next block is the only one to be rewarded. As the riddles are progressively more difficult to solve, more computational power is required, putting miners in a competition for resources.
Miners have settled on two main operational models: Farms, which are large datacenters usually filled with dedicated hardware; and Pools, which join together thousands of single users to share computational power (with a fee to the Pool manager), increasing the probability of mining success.
4. Third-party Service Providers run businesses on the Bitcoin network for Bitcoin users. The largest such actors are Exchanges, which hold both cryptocurrency and traditional currency (fiat), and allow users to trade on their systems. Exchanges implement Know Your Customer (KYC) procedures and have bank accounts to store fiat, keeping track of users’ transactions on their databases.
We ground this discussion on Bitcoin, the oldest and most widespread cryptocurrency, which also has by far the highest capitalization. Although there are fundamental and nuanced differences between cryptocurrencies (such as alternative verification methods and additional encryption levels), the key principle are largely transferable.
How secure is Bitcoin? A number of known attacks have exposed vulnerabilities that could conceivably hamstring Bitcoin to the point where there is no more value in “extracting” new coins and the value of existing Bitcoins plummets. For example:
Computational-power control—the 51-percent attack. While some attacks are designed to steal Bitcoins, others aim at disrupting the entire network. When one actor controls 51 percent or more of Bitcoin’s computational resources (“hashrate”), it gains decision-making power over current transactions. Although it would not be possible, for example, to reverse other people’s transactions or steal from users’ accounts, an a 51 -percent controlling stake could interfere with the process of recording new blocks and thus possibly: (1) reverse transactions in process (2) prevent confirmation of transactions; and (3) prevent other miners from participating. In this scenario, users’ confidence would plummet, as would the value of Bitcoins.
This is not a far-fetched liability. For one, it already happened in 2014. More importantly, three actors based in China currently control ca. 55 percent of the Bitcoin mining market. Were they to coalesce as one actor, they would in effect control the Bitcoin market. While scaling up 51 percent of hashrate power from scratch is still feasible, it is not cheap.
While miners and developers have been aware of the possibility of a 51 percent attack and takeover since the inception of Bitcoin, as of today no definitive and reliable solution has been put forward.
The Bitcoin network’s hosting is extremely centralized: one-third of the network is hosted by only 13 ISPs (out of the approximately 50,000 ISPs in the world), and three of them together handle 60 percent of all Bitcoin traffic
Partitioning Bitcoin by blocking ISPs. Bitcoin actors exchange transactions and blocks on the Internet through Internet Service Providers (ISPs). But the Bitcoin network’s hosting is extremely centralized: one-third of the network is hosted by only 13 ISPs (out of the approximately 50,000 ISPs in the world), and three of them together handle 60 percent of all Bitcoin traffic. This is not negative per se, but such centralization makes Bitcoin vulnerable to routing attacks. A handful of ISPs or governments with a mandate could stop or slow down communication at scale, effectively cutting Bitcoin into smaller sub-networks (“partitions”) with a fraction of the computing power and without the capability to make transactions. Miners and startups are envisioning ways to decrease dependency on ISPs. Blockstream, a prominent Bitcoin developer, raised $76 million in 2016 and is now renting satellite bandwidth to beam blocks through space rather than ISPs, but it is still debated whether the community will accept blocks streamed by a single counterparty.
Denial of service attacks to destabilize computational power. Third-party service providers orchestrate allocation of computational workloads to Pools, which represent the majority of “mining” power. On the Internet, these Pools are subject to Distributed Denial of Service (DDoS) attacks. When an attack knocks a Pool offline, its participants either wait to go back online, or join a different Pool to restart earning revenues. Because of this dynamic, Pools are frequently targeted by attackers, both ransom-seeking criminals and competing Pools that aim at “stealing” share of the system’s computational power. The most prominent example is the GHash.io case: in March 2015; a DDoS attack took it offline for six hours. GHash.io, once the largest Pool in Bitcoin, which at one point had 50 percent of the hashrate, has never recovered.
Compromising Wallets and Exchanges to unveil anonymity. Users who choose not to set up their own full Node in order to trade—which gives them complete anonymity in all transactions—have to trust third parties to hold their Bitcoin Wallets. These third-party Exchanges, which exchange cryptocurrencies and regular currencies, manage sensitive information, such as users’ identity and private keys, and are easily breached if they don’t invest in robust security solutions.
Without his own Node, a user on an Exchange is not protected by the blockchain, but is trusting the third-party to: (1) hold his traditional money account; (2) hold his crypto-currency account; (3) correctly record transactions; and (4) secure his private keys and personal information. The issue is compounded by the fact that Bitcoin transactions are by nature irreversible; losing private keys, sending incorrect transactions, or being victim of a fraud means losing those Bitcoins forever.
Even though Exchanges are typically KYC-compliant in their legal jurisdiction, they hold large amounts of Bitcoins and are typically young, under-capitalized ventures with limited cyber-security measures in place. Like the Coincheck Exchange in Japan, the MtGox Exchange, for example, lost 900,000 Bitcoins in 2014 valued at $400 million because of security breaches (when the total amount of Bitcoin was circa 11.5 million).
Indeed, other “common” trojan/phishing/ransomware attacks can be leveraged to steal or ransom Bitcoins from users. In a Sybil attack, for example, an attacker sets up nodes that “screen” the attacked node from the rest of the network, which prevents the victim from making transactions.
Bitcoin transactions are by nature irreversible; losing private keys, sending incorrect transactions, or being victim of a fraud means losing those Bitcoins forever
Developers lack governance. Modifications to the Bitcoin protocol and software are debated and defined through discussions on forums, social networks, and at conferences. Anyone who disagrees with the proposed changes and has a sufficient number of followers can fork his own version of the chain (such as Bitcoin cash), or establish his own cryptocurrency, by applying modifications to the original code.
Today, few people have commit rights on Bitcoin Core, the software used by 90 percent of Bitcoin network actors. In principle, this is a sustainable model, as shown by Linux community, but an adequate governance structure is still missing, especially for a cryptocurrency that potentially aims at becoming a global alternative-payment method.
Sustainability and scalability. Blockchain technology has great potential that is being applied in a variety of financial and business projects. But cryptocurrencies must resolve a number of questions and issues before we can consider the architecture reliable and secure.
Two other issues to consider are the sustainability and scalability of Bitcoin, and the economics of Bitcoin (we’ll address these in future Digital Bytes). As more computational power is required, the sustainability of the network is jeopardized, while hardware and energy costs could potentially put many miners out of business, rendering Bitcoin to a 51 percent winner.